- 3Gateway Configuration
- 4Client Configuration
- 4.3Authentication Tab
Introduction
This guide provides information that can be used to configure a Cisco PIX/ASA device running firmware version 7.x to support IPsec VPN client connectivity. If you have a PIX device running firmware version 6.x, please consult the HowtoCiscoPix. The Shrew Soft VPN Client has been tested with Cisco products to ensure interoperability.
Overview
The configuration example described below will allow an IPsec VPN client to communicate with a single remote private network. The client uses the pull configuration method to acquire the following parameters automatically from the gateway.
- IP Address
- IP Netmask
- DNS Servers
- DNS Default Domain Suffix
- DNS Split Network Domain List
- WINS Servers
- PFS Group
- Remote Network Topology
- Login Banner
Upgrading - Uploading AnyConnect Secure Mobility Client v4.x SSL VPN on Cisco ASA 5506-X, 5508-X, 5512-X, 5515-X, 5516-X, 5525-X, 5545-X, 5555-X, 5585-X. Written by Administrator. Posted in Cisco Firewalls - ASA & PIX Firewall Configuration. Just to add what @Rob Ingram mentioned you have to make sure the version is compatiable. I have seem many issues the client is running anyconnect version 4.8 but on the ASA the headend is configured as anyconnect 4.7. Some client can connect to ASA with anyconnect 4.8 but other having issues. Apr 24, 2020 This document describes how to configure an Adaptive Security Appliance (ASA) as the VPN gateway accepts connections from the Cisco AnyConnect Secure Mobility Client through Management VPN tunnel.
Gateway Configuration
This example assumes you have knowledge of the Cisco ASA gateway command line configuration interface. For more information, please consult your Cisco product documentation.
- 21 thoughts on ' Using the Cisco ASA 5505 as a VPN server with the Cisco VPN Client software ' Trond May 15, 2012 at 10:29 am. Is it so that I shall put the DNS-server IP-address from the outside – as in – for instance 8.8.8.8 (the google dns server addresses).
- ASA 5585-X IPS Security Services Processor. ASA Advanced Inspection and Prevention (AIP) Security Services Module. ASA Advanced Inspection and Prevention Security Services Card. ASA Content Security and Control (CSC) Security Services Module. Catalyst 6500 Series / 7600 Series ASA Services Module.
Interfaces
Two network interfaces are configured. The outside interface has a static public IP address of 1.1.1.20 which faces the internet. The inside interface has a static private IP address that faces the internal private network. The default gateway is configured as 1.1.1.3 via the outside interface.
Access List
An access lists must be configured to define the IPSec policies. This is expressed with the source matching the local private network(s) and the destination matching any as the VPN client address will be assigned by the gateway.
Address Pool
The IP address pool must be configured. Clients will be assigned private network addresses from a pool of 10.2.20.1-10.2.20.126.
User Authentication
User authentication must be configured to support IKE extended authentication ( XAuth ). In this example, we use define user accounts locally on the ASA. It is possible to pass this authentication to a radius or an LDAP account server using the Cisco AAA authentication mechanism. For more information, please consult your cisco product documentation.
IPsec Parameters
A transform set and dynamic IPsec crypto map must be configured to support client VPN connections. The dynamic crypto map is then assigned to a standard crypto map and bound to the outside ( public ) interface.
ISAKMP Parameters
The ISAKMP protocol must be enabled on the outside ( public ) interface and an ISAKMP policy must be configured. NAT Traversal is also enabled to allow clients to communicate effectively when their peer address is being translated. The keep alive packet rate is set to 20 seconds.
SSL VPN Client (SVC) On IOS With SDM Configuration Example
Group Policy
A group policy must be configured to provide the client with dynamic configuration information.
Tunnel Group
A tunnel group must be configured to define the VPN Client tunnel parameters. It is created using the type ipsec-ra for IPsec remote access. The client uses the tunnel group name as its FQDN identity value and the tunnel group pre-shared-key as its pre-shared key value.
Client Configuration
The client configuration in this example is straight forward. Open the Access Manager application and create a new site configuration. Configure the settings listed below in the following tabs.
General Tab
The Remote Host section must be configured. The Host Name or IP Address is defined as 10.1.1.20 to match the ASA outside ( public ) interface address. The Auto Configuration mode should be set to ike config pull.
PIX/ASA 7.x As A Remote VPN Server Using ASDM Configuration Example

Phase 1 Tab
The Proposal section must be configured. The Exchange Type is set to aggressive and the DH Exchange is set to group 2 to match the ASA ISAKMP policy definition.
Authentication Tab
The client authentication settings must be configured. The Authentication Method is defined as Mutual PSK + XAuth.
Local Identity Tab
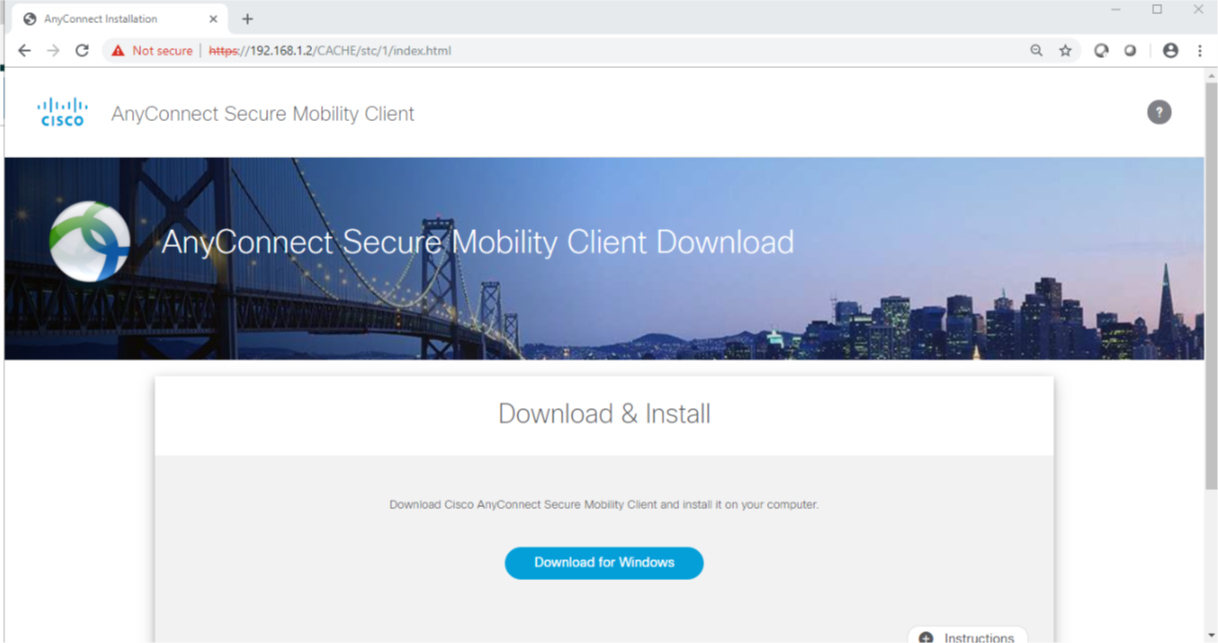
The Local Identity parameters are defined as Fully Qualified Domain Name with a FQDN String of 'vpnclient' to match the ASA tunnel group name.
Remote Identity Tab
The Remote Identity parameters are set to IP Address with the Use a discovered remote host address option checked to match the ASA ISAKMP identity parameter.
Credentials Tab
The Credentials Pre Shared Key is defined as 'mypresharedkey' to match the ASA tunnel group pre-shared-key.
Known Issues
Cisco gateways support a proprietary form of hybrid authentication which does not conform to RFC draft standards. At this time the Shrew Soft VPN Client does not support this authentication mode. We hope to add support for this in the future.
Resources
Media:Ciscoasa.cfg.txt
Media:Ciscoasa.vpn.txt
Thanks to technology in today's world many people have the luxury of working remote. Today we will discuss configuring a Cisco ASA 5506-X for Client Remote Access VPN. Below is the copy and paste config
Copy and paste config
SRG-ASA# show run
ASA Version 9.4(1)
ip local pool VPN_Pool 192.168.1.100-192.168.1.120 mask 255.255.255.0
!
interface GigabitEthernet1/2
nameif inside
security-level 100
ip address 192.168.0.1 255.255.255.0
!
access-list split standard permit 192.168.0.0 255.255.255.0
access-list ra-split standard permit 192.168.0.0 255.255.255.0
access-list ra-split-nonat extended permit ip 192.168.0.0 255.255.255.0 192.168.1.0 255.255.255.0
user-identity default-domain LOCAL
aaa authentication ssh console LOCAL
no snmp-server location
no snmp-server contact
sysopt connection tcpmss 1387
crypto ipsec ikev1 transform-set ESP-3DES-MD5 esp-3des esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-AES-256-MD5 esp-aes-256 esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-DES-SHA esp-des esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-DES-MD5 esp-des esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-AES-192-MD5 esp-aes-192 esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-AES-256-SHA esp-aes-256 esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-128-SHA esp-aes esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-192-SHA esp-aes-192 esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-128-MD5 esp-aes esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-3DES-SHA esp-3des esp-sha-hmac
crypto ipsec ikev1 transform-set myset esp-3des esp-sha-hmac
crypto ipsec ikev1 transform-set myset mode transport
crypto ipsec ikev1 transform-set L2TP-tunnel esp-3des esp-sha-hmac
crypto ipsec ikev1 transform-set L2TP-tunnel mode transport
crypto ipsec ikev1 transform-set ESP-AES-128-SHA-TRANS esp-aes esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-128-SHA-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-AES-128-MD5-TRANS esp-aes esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-AES-128-MD5-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-AES-192-SHA-TRANS esp-aes-192 esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-192-SHA-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-AES-192-MD5-TRANS esp-aes-192 esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-AES-192-MD5-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-AES-256-SHA-TRANS esp-aes-256 esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-256-SHA-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-AES-256-MD5-TRANS esp-aes-256 esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-AES-256-MD5-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-3DES-SHA-TRANS esp-3des esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-3DES-SHA-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-3DES-MD5-TRANS esp-3des esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-3DES-MD5-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-DES-SHA-TRANS esp-des esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-DES-SHA-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-DES-MD5-TRANS esp-des esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-DES-MD5-TRANS mode transport
crypto ipsec ikev1 transform-set transform-amzn esp-aes esp-sha-hmac
crypto ipsec ikev2 ipsec-proposal DES
protocol esp encryption des
protocol esp integrity sha-1 md5
crypto ipsec ikev2 ipsec-proposal 3DES
protocol esp encryption 3des
protocol esp integrity sha-1 md5
crypto ipsec ikev2 ipsec-proposal AES
protocol esp encryption aes
protocol esp integrity sha-1 md5
crypto ipsec ikev2 ipsec-proposal AES192
protocol esp encryption aes-192
protocol esp integrity sha-1 md5
crypto ipsec ikev2 ipsec-proposal AES256
protocol esp encryption aes-256
protocol esp integrity sha-1 md5
crypto ipsec security-association lifetime seconds 3600
crypto ipsec security-association replay window-size 128
crypto ipsec security-association pmtu-aging infinite
crypto ipsec df-bit clear-df outside
crypto dynamic-map SYSTEM_DEFAULT_CRYPTO_MAP 65533 set ikev1 transform-set L2TP-tunnel ESP-AES-128-SHA ESP-AES-128-MD5 ESP-AES-192-SHA ESP-AES-192-MD5 ESP-AES-256-SHA ESP-AES-256-MD5 ESP-3DES-SHA ESP-3DES-MD5 ESP-DES-SHA ESP-DES-MD5
crypto dynamic-map SYSTEM_DEFAULT_CRYPTO_MAP 65534 set ikev1 transform-set myset ESP-AES-128-SHA ESP-AES-128-MD5 ESP-AES-192-SHA ESP-AES-192-MD5 ESP-AES-256-SHA ESP-AES-256-MD5 ESP-3DES-SHA ESP-3DES-MD5 ESP-DES-SHA ESP-DES-MD5
crypto dynamic-map SYSTEM_DEFAULT_CRYPTO_MAP 65535 set pfs
crypto dynamic-map SYSTEM_DEFAULT_CRYPTO_MAP 65535 set ikev1 transform-set ESP-AES-128-SHA ESP-AES-128-MD5 ESP-AES-192-SHA ESP-AES-192-MD5 ESP-AES-256-SHA ESP-AES-256-MD5 ESP-3DES-SHA ESP-3DES-MD5 ESP-DES-SHA ESP-DES-MD5 myset
crypto dynamic-map SYSTEM_DEFAULT_CRYPTO_MAP 65535 set ikev2 ipsec-proposal AES256 AES192 AES 3DES DES
crypto map SRG_VPN 64553 ipsec-isakmp dynamic SYSTEM_DEFAULT_CRYPTO_MAP
crypto map SRG_VPN interface outside
crypto ca trustpool policy
crypto isakmp identity address
crypto ikev2 policy 1
encryption aes-256
integrity sha
group 2
prf sha
lifetime seconds 28800
crypto ikev2 policy 2
encryption aes-256
integrity sha256
group 2
prf sha
lifetime seconds 28800
crypto ikev2 policy 3
encryption aes-256
integrity sha
group 2
prf sha256
lifetime seconds 28800
crypto ikev2 policy 5
encryption aes-256
integrity sha256
group 2
prf sha256
lifetime seconds 28800
crypto ikev2 policy 10
encryption aes-192
integrity sha
group 5 2
prf sha
lifetime seconds 86400
crypto ikev2 policy 20
encryption aes
integrity sha
group 5 2
prf sha
lifetime seconds 86400
crypto ikev2 policy 30
encryption 3des
integrity sha
group 5 2
prf sha
lifetime seconds 86400
crypto ikev2 policy 40
encryption des
integrity sha
group 5 2
prf sha
lifetime seconds 86400
crypto ikev2 enable outside
crypto ikev2 enable inside
crypto ikev1 enable outside
crypto ikev1 enable inside
crypto ikev1 policy 1
authentication pre-share
encryption 3des
hash md5
group 2
lifetime 86400
crypto ikev1 policy 2
authentication pre-share
encryption aes-256
hash sha
group 2
lifetime 28800
crypto ikev1 policy 5
authentication pre-share
encryption aes-192
hash sha
group 2
lifetime 28800
crypto ikev1 policy 10
authentication pre-share
encryption aes
hash sha
group 2
lifetime 86400
crypto ikev1 policy 20
authentication pre-share
encryption 3des
hash sha
group 2
lifetime 86400
crypto ikev1 policy 200
authentication pre-share
encryption 3des
hash sha
group 2
lifetime 28800
crypto ikev1 policy 201
authentication pre-share
encryption aes
hash sha
group 2
lifetime 28800
!
dhcpd address 192.168.0.100-192.168.0.200 inside
dhcpd domain surge.local interface inside
dhcpd update dns interface inside
dhcpd enable inside
!
username jgranados password zI/d0As121029oXGg encrypted privilege 15
username jgranados attributes (<–Shouldn't need attributes but doesn't hurt to add)
vpn-group-policy DfltGrpPolicy
!
group-policy DfltGrpPolicy attributes
dns-server value 8.8.8.8 8.8.4.4
vpn-tunnel-protocol ikev1 l2tp-ipsec ssl-client ssl-clientless
ipsec-udp enable
split-tunnel-policy tunnelspecified
split-tunnel-network-list value ra-split ( group-policy filter internal
dynamic-access-policy-record DfltAccessPolicy
tunnel-group DefaultRAGroup general-attributes
address-pool VPN_Pool
tunnel-group DefaultRAGroup ipsec-attributes
ikev1 pre-shared-key SECRET
tunnel-group DefaultRAGroup ppp-attributes
authentication ms-chap-v2
SRG-ASA#
Configuring MAC VPN Client
Many users are now using MAC clients. Below you will find step by step instructions on configuring a MAC Client for VPN Remote Access.
1. Open 'System Preferences' and go to 'Network'. Choose the add setting highlighted below, then select VPN.
2. Configure the following VPN interface with the following settings
INTERFACE: VPN
VPN TYPE: CISCO IPSEC
SERVICE NAME: (Preferably Company Name or Easy to Remember Description)
3. Select 'Authentication Settings' and type your as the shared secret. Leave group name empty and choose ok.
Cisco compatible vpn client for windows 10. Aug 29, 2019 The following third-party vendors offer VPN clients for Windows Mobile that work with the Cisco ASA 5500 series: Antha, Apani, Bluefire, Microsoft, and NCP.DE. Cisco supports the Microsoft client; the respective vendors support the other clients. Cisco VPN Client Compatibility. The remote VPN client can be a Cisco device acting as a Cisco VPN hardware client or a PC running the Cisco VPN Client software (Release 4.x or 5.x). The Cisco VPN Client software is an IPsec client software for Windows, Mac, or Linux users. The Cisco VPN Client software is compatible with the following platforms.
Overview
The configuration example described below will allow an IPsec VPN client to communicate with a single remote private network. The client uses the pull configuration method to acquire the following parameters automatically from the gateway.
- IP Address
- IP Netmask
- DNS Servers
- DNS Default Domain Suffix
- DNS Split Network Domain List
- WINS Servers
- PFS Group
- Remote Network Topology
- Login Banner
Upgrading - Uploading AnyConnect Secure Mobility Client v4.x SSL VPN on Cisco ASA 5506-X, 5508-X, 5512-X, 5515-X, 5516-X, 5525-X, 5545-X, 5555-X, 5585-X. Written by Administrator. Posted in Cisco Firewalls - ASA & PIX Firewall Configuration. Just to add what @Rob Ingram mentioned you have to make sure the version is compatiable. I have seem many issues the client is running anyconnect version 4.8 but on the ASA the headend is configured as anyconnect 4.7. Some client can connect to ASA with anyconnect 4.8 but other having issues. Apr 24, 2020 This document describes how to configure an Adaptive Security Appliance (ASA) as the VPN gateway accepts connections from the Cisco AnyConnect Secure Mobility Client through Management VPN tunnel.
Gateway Configuration
This example assumes you have knowledge of the Cisco ASA gateway command line configuration interface. For more information, please consult your Cisco product documentation.
- 21 thoughts on ' Using the Cisco ASA 5505 as a VPN server with the Cisco VPN Client software ' Trond May 15, 2012 at 10:29 am. Is it so that I shall put the DNS-server IP-address from the outside – as in – for instance 8.8.8.8 (the google dns server addresses).
- ASA 5585-X IPS Security Services Processor. ASA Advanced Inspection and Prevention (AIP) Security Services Module. ASA Advanced Inspection and Prevention Security Services Card. ASA Content Security and Control (CSC) Security Services Module. Catalyst 6500 Series / 7600 Series ASA Services Module.
Interfaces
Two network interfaces are configured. The outside interface has a static public IP address of 1.1.1.20 which faces the internet. The inside interface has a static private IP address that faces the internal private network. The default gateway is configured as 1.1.1.3 via the outside interface.
Access List
An access lists must be configured to define the IPSec policies. This is expressed with the source matching the local private network(s) and the destination matching any as the VPN client address will be assigned by the gateway.
Address Pool
The IP address pool must be configured. Clients will be assigned private network addresses from a pool of 10.2.20.1-10.2.20.126.
User Authentication
User authentication must be configured to support IKE extended authentication ( XAuth ). In this example, we use define user accounts locally on the ASA. It is possible to pass this authentication to a radius or an LDAP account server using the Cisco AAA authentication mechanism. For more information, please consult your cisco product documentation.
IPsec Parameters
A transform set and dynamic IPsec crypto map must be configured to support client VPN connections. The dynamic crypto map is then assigned to a standard crypto map and bound to the outside ( public ) interface.
ISAKMP Parameters
The ISAKMP protocol must be enabled on the outside ( public ) interface and an ISAKMP policy must be configured. NAT Traversal is also enabled to allow clients to communicate effectively when their peer address is being translated. The keep alive packet rate is set to 20 seconds.
SSL VPN Client (SVC) On IOS With SDM Configuration Example
Group Policy
A group policy must be configured to provide the client with dynamic configuration information.
Tunnel Group
A tunnel group must be configured to define the VPN Client tunnel parameters. It is created using the type ipsec-ra for IPsec remote access. The client uses the tunnel group name as its FQDN identity value and the tunnel group pre-shared-key as its pre-shared key value.
Client Configuration
The client configuration in this example is straight forward. Open the Access Manager application and create a new site configuration. Configure the settings listed below in the following tabs.
General Tab
The Remote Host section must be configured. The Host Name or IP Address is defined as 10.1.1.20 to match the ASA outside ( public ) interface address. The Auto Configuration mode should be set to ike config pull.
PIX/ASA 7.x As A Remote VPN Server Using ASDM Configuration Example
Phase 1 Tab
The Proposal section must be configured. The Exchange Type is set to aggressive and the DH Exchange is set to group 2 to match the ASA ISAKMP policy definition.
Authentication Tab
The client authentication settings must be configured. The Authentication Method is defined as Mutual PSK + XAuth.
Local Identity Tab
The Local Identity parameters are defined as Fully Qualified Domain Name with a FQDN String of 'vpnclient' to match the ASA tunnel group name.
Remote Identity Tab
The Remote Identity parameters are set to IP Address with the Use a discovered remote host address option checked to match the ASA ISAKMP identity parameter.
Credentials Tab
The Credentials Pre Shared Key is defined as 'mypresharedkey' to match the ASA tunnel group pre-shared-key.
Known Issues
Cisco gateways support a proprietary form of hybrid authentication which does not conform to RFC draft standards. At this time the Shrew Soft VPN Client does not support this authentication mode. We hope to add support for this in the future.
Resources
Media:Ciscoasa.cfg.txt
Media:Ciscoasa.vpn.txt
Thanks to technology in today's world many people have the luxury of working remote. Today we will discuss configuring a Cisco ASA 5506-X for Client Remote Access VPN. Below is the copy and paste config
Copy and paste config
SRG-ASA# show run
ASA Version 9.4(1)
ip local pool VPN_Pool 192.168.1.100-192.168.1.120 mask 255.255.255.0
!
interface GigabitEthernet1/2
nameif inside
security-level 100
ip address 192.168.0.1 255.255.255.0
!
access-list split standard permit 192.168.0.0 255.255.255.0
access-list ra-split standard permit 192.168.0.0 255.255.255.0
access-list ra-split-nonat extended permit ip 192.168.0.0 255.255.255.0 192.168.1.0 255.255.255.0
user-identity default-domain LOCAL
aaa authentication ssh console LOCAL
no snmp-server location
no snmp-server contact
sysopt connection tcpmss 1387
crypto ipsec ikev1 transform-set ESP-3DES-MD5 esp-3des esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-AES-256-MD5 esp-aes-256 esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-DES-SHA esp-des esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-DES-MD5 esp-des esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-AES-192-MD5 esp-aes-192 esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-AES-256-SHA esp-aes-256 esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-128-SHA esp-aes esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-192-SHA esp-aes-192 esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-128-MD5 esp-aes esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-3DES-SHA esp-3des esp-sha-hmac
crypto ipsec ikev1 transform-set myset esp-3des esp-sha-hmac
crypto ipsec ikev1 transform-set myset mode transport
crypto ipsec ikev1 transform-set L2TP-tunnel esp-3des esp-sha-hmac
crypto ipsec ikev1 transform-set L2TP-tunnel mode transport
crypto ipsec ikev1 transform-set ESP-AES-128-SHA-TRANS esp-aes esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-128-SHA-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-AES-128-MD5-TRANS esp-aes esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-AES-128-MD5-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-AES-192-SHA-TRANS esp-aes-192 esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-192-SHA-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-AES-192-MD5-TRANS esp-aes-192 esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-AES-192-MD5-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-AES-256-SHA-TRANS esp-aes-256 esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-AES-256-SHA-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-AES-256-MD5-TRANS esp-aes-256 esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-AES-256-MD5-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-3DES-SHA-TRANS esp-3des esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-3DES-SHA-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-3DES-MD5-TRANS esp-3des esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-3DES-MD5-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-DES-SHA-TRANS esp-des esp-sha-hmac
crypto ipsec ikev1 transform-set ESP-DES-SHA-TRANS mode transport
crypto ipsec ikev1 transform-set ESP-DES-MD5-TRANS esp-des esp-md5-hmac
crypto ipsec ikev1 transform-set ESP-DES-MD5-TRANS mode transport
crypto ipsec ikev1 transform-set transform-amzn esp-aes esp-sha-hmac
crypto ipsec ikev2 ipsec-proposal DES
protocol esp encryption des
protocol esp integrity sha-1 md5
crypto ipsec ikev2 ipsec-proposal 3DES
protocol esp encryption 3des
protocol esp integrity sha-1 md5
crypto ipsec ikev2 ipsec-proposal AES
protocol esp encryption aes
protocol esp integrity sha-1 md5
crypto ipsec ikev2 ipsec-proposal AES192
protocol esp encryption aes-192
protocol esp integrity sha-1 md5
crypto ipsec ikev2 ipsec-proposal AES256
protocol esp encryption aes-256
protocol esp integrity sha-1 md5
crypto ipsec security-association lifetime seconds 3600
crypto ipsec security-association replay window-size 128
crypto ipsec security-association pmtu-aging infinite
crypto ipsec df-bit clear-df outside
crypto dynamic-map SYSTEM_DEFAULT_CRYPTO_MAP 65533 set ikev1 transform-set L2TP-tunnel ESP-AES-128-SHA ESP-AES-128-MD5 ESP-AES-192-SHA ESP-AES-192-MD5 ESP-AES-256-SHA ESP-AES-256-MD5 ESP-3DES-SHA ESP-3DES-MD5 ESP-DES-SHA ESP-DES-MD5
crypto dynamic-map SYSTEM_DEFAULT_CRYPTO_MAP 65534 set ikev1 transform-set myset ESP-AES-128-SHA ESP-AES-128-MD5 ESP-AES-192-SHA ESP-AES-192-MD5 ESP-AES-256-SHA ESP-AES-256-MD5 ESP-3DES-SHA ESP-3DES-MD5 ESP-DES-SHA ESP-DES-MD5
crypto dynamic-map SYSTEM_DEFAULT_CRYPTO_MAP 65535 set pfs
crypto dynamic-map SYSTEM_DEFAULT_CRYPTO_MAP 65535 set ikev1 transform-set ESP-AES-128-SHA ESP-AES-128-MD5 ESP-AES-192-SHA ESP-AES-192-MD5 ESP-AES-256-SHA ESP-AES-256-MD5 ESP-3DES-SHA ESP-3DES-MD5 ESP-DES-SHA ESP-DES-MD5 myset
crypto dynamic-map SYSTEM_DEFAULT_CRYPTO_MAP 65535 set ikev2 ipsec-proposal AES256 AES192 AES 3DES DES
crypto map SRG_VPN 64553 ipsec-isakmp dynamic SYSTEM_DEFAULT_CRYPTO_MAP
crypto map SRG_VPN interface outside
crypto ca trustpool policy
crypto isakmp identity address
crypto ikev2 policy 1
encryption aes-256
integrity sha
group 2
prf sha
lifetime seconds 28800
crypto ikev2 policy 2
encryption aes-256
integrity sha256
group 2
prf sha
lifetime seconds 28800
crypto ikev2 policy 3
encryption aes-256
integrity sha
group 2
prf sha256
lifetime seconds 28800
crypto ikev2 policy 5
encryption aes-256
integrity sha256
group 2
prf sha256
lifetime seconds 28800
crypto ikev2 policy 10
encryption aes-192
integrity sha
group 5 2
prf sha
lifetime seconds 86400
crypto ikev2 policy 20
encryption aes
integrity sha
group 5 2
prf sha
lifetime seconds 86400
crypto ikev2 policy 30
encryption 3des
integrity sha
group 5 2
prf sha
lifetime seconds 86400
crypto ikev2 policy 40
encryption des
integrity sha
group 5 2
prf sha
lifetime seconds 86400
crypto ikev2 enable outside
crypto ikev2 enable inside
crypto ikev1 enable outside
crypto ikev1 enable inside
crypto ikev1 policy 1
authentication pre-share
encryption 3des
hash md5
group 2
lifetime 86400
crypto ikev1 policy 2
authentication pre-share
encryption aes-256
hash sha
group 2
lifetime 28800
crypto ikev1 policy 5
authentication pre-share
encryption aes-192
hash sha
group 2
lifetime 28800
crypto ikev1 policy 10
authentication pre-share
encryption aes
hash sha
group 2
lifetime 86400
crypto ikev1 policy 20
authentication pre-share
encryption 3des
hash sha
group 2
lifetime 86400
crypto ikev1 policy 200
authentication pre-share
encryption 3des
hash sha
group 2
lifetime 28800
crypto ikev1 policy 201
authentication pre-share
encryption aes
hash sha
group 2
lifetime 28800
!
dhcpd address 192.168.0.100-192.168.0.200 inside
dhcpd domain surge.local interface inside
dhcpd update dns interface inside
dhcpd enable inside
!
username jgranados password zI/d0As121029oXGg encrypted privilege 15
username jgranados attributes (<–Shouldn't need attributes but doesn't hurt to add)
vpn-group-policy DfltGrpPolicy
!
group-policy DfltGrpPolicy attributes
dns-server value 8.8.8.8 8.8.4.4
vpn-tunnel-protocol ikev1 l2tp-ipsec ssl-client ssl-clientless
ipsec-udp enable
split-tunnel-policy tunnelspecified
split-tunnel-network-list value ra-split ( group-policy filter internal
dynamic-access-policy-record DfltAccessPolicy
tunnel-group DefaultRAGroup general-attributes
address-pool VPN_Pool
tunnel-group DefaultRAGroup ipsec-attributes
ikev1 pre-shared-key SECRET
tunnel-group DefaultRAGroup ppp-attributes
authentication ms-chap-v2
SRG-ASA#
Configuring MAC VPN Client
Many users are now using MAC clients. Below you will find step by step instructions on configuring a MAC Client for VPN Remote Access.
1. Open 'System Preferences' and go to 'Network'. Choose the add setting highlighted below, then select VPN.
2. Configure the following VPN interface with the following settings
INTERFACE: VPN
VPN TYPE: CISCO IPSEC
SERVICE NAME: (Preferably Company Name or Easy to Remember Description)
3. Select 'Authentication Settings' and type your as the shared secret. Leave group name empty and choose ok.
Cisco compatible vpn client for windows 10. Aug 29, 2019 The following third-party vendors offer VPN clients for Windows Mobile that work with the Cisco ASA 5500 series: Antha, Apani, Bluefire, Microsoft, and NCP.DE. Cisco supports the Microsoft client; the respective vendors support the other clients. Cisco VPN Client Compatibility. The remote VPN client can be a Cisco device acting as a Cisco VPN hardware client or a PC running the Cisco VPN Client software (Release 4.x or 5.x). The Cisco VPN Client software is an IPsec client software for Windows, Mac, or Linux users. The Cisco VPN Client software is compatible with the following platforms.
4. Input you outside interface IP address as the server address, or if you've created a DNS entry you can also use that. You can also select 'Show VPN status in the menu bar' which makes it a lot easier to connect in the future. Then Connect.
5. After Connecting the SURGE connection will show green like this.

